What is Virtualization ?
| Tweet |
Virtualization is a way of creating a virtual (rather than physical) version of something, including virtual computer hardware platforms , operating systems, storage devices, and computer network resources. Some of the benefits of using virtualization are:
• Eco friendliness : How can virtualization be eco-friendly? It’s simple, in the absence of virtualization, more and more physical systems are required in the data center. To keep these systems cool, powerful air-conditioning systems are required, which contribute to global warming. With virtualization, a single server can run multiple instances of an operating system simultaneously, reducing the number of physical devices in the data center. • Reduced cost: When there’s a need to expand a data center, the cost of procuring new hardware can be considerable. But with virtualization solutions, the same hardware can be reused optimally to accommodate expansion needs. Hence, it clearly saves the cost involved in purchasing new hardware. • Faster deployment: Suppose there’s a demand for a new web server. In a physical data center, the IT team would have to set up the hardware and then the software. It would take some time for the entire process. But with virtualization, servers can be created and running within few minutes and the applications can be deployed instantly. This saves lot of time and effort. Hypervisors A hypervisor is a piece of computer software, firmware, or hardware that creates, runs, and manages virtual machines. A system on which a hypervisor is running one or more virtual machines is called a host machine . Every virtual machine that runs on a hypervisor is known as a guest machine . The hypervisor is responsible for providing the guest operating systems with a virtual operating platform, and it manages their execution. The Type 1 HypervisorA : Type 1 hypervisor is also known as a bare metal hypervisor. It resides directly on the hardware and makes resources available for the guest operating systems. Type 2 Hypervisor A : Type 2 hypervisor resides on a base operating system and supports the hosting of other guest operating systems .There is a risk that if the base operating system encounters any errors, the entire virtualization stack (the guest operating systems) might crash. Reasons to use virtualization Virtualization allows you to:
There are three versions of Hyper-V available:
Common Security Issues with Virtual Machines In addition to the security issues in the guest system hosted in a virtual environment, the virtualization environment itself adds to certain security concerns, as described next: • Unpatched Hypervisor: The hypervisor that is used to run a virtual machine is a piece of code and might be vulnerable to security issues. Often the hypervisor is not updated and patched, leaving it vulnerable to attackers. Once the hypervisor is compromised, an attacker may be able to compromise the virtual machines hosted on that vulnerable hypervisor. • Insecure Management Console: Every virtualization platform has a management console or user interface through which the administrator can perform various activities, like starting or stopping the virtual machines. However this management console may be vulnerable to various security issues like XSS, privilege escalation, weak password policy, and so on. Such insecure management console would provide easy entry point to the attackers. |
|
• Eco friendliness : How can virtualization be eco-friendly? It’s simple, in the absence of virtualization, more and more physical systems are required in the data center. To keep these systems cool, powerful air-conditioning systems are required, which contribute to global warming. With virtualization, a single server can run multiple instances of an operating system simultaneously, reducing the number of physical devices in the data center.
• Reduced cost: When there’s a need to expand a data center, the cost of procuring new hardware can be considerable. But with virtualization solutions, the same hardware can be reused optimally to accommodate expansion needs. Hence, it clearly saves the cost involved in purchasing new hardware.
• Faster deployment: Suppose there’s a demand for a new web server. In a physical data center, the IT team would have to set up the hardware and then the software. It would take some time for the entire process. But with virtualization, servers can be created and running within few minutes and the applications can be deployed instantly. This saves lot of time and effort.
Hypervisors
A hypervisor is a piece of computer software, firmware, or hardware that creates, runs, and manages virtual machines.
A system on which a hypervisor is running one or more virtual machines is called a host machine . Every virtual machine that runs on a hypervisor is known as a guest machine . The hypervisor is responsible for providing the guest operating systems with a virtual operating platform, and it manages their execution.
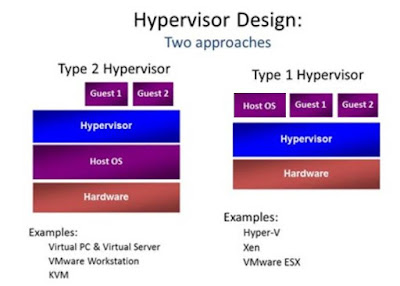
The Type 1 HypervisorA :
Type 1 hypervisor is also known as a bare metal hypervisor. It resides directly on the hardware and makes resources available for the guest operating systems.
Type 2 Hypervisor A :
Type 2 hypervisor resides on a base operating system and supports the hosting of other guest operating systems .There is a risk that if the base operating system encounters any errors, the entire virtualization stack (the guest operating systems) might crash.
Reasons to use virtualization
Virtualization allows you to:
Run software that requires an older versions of Windows or non-Windows operating systems.
Experiment with other operating systems. Hyper-V makes it very easy to create and remove different operating systems.
Test software on multiple operating systems using multiple virtual machines. With Hyper-V, you can run them all on a single desktop or laptop computer. These virtual machines can be exported and then imported into any other Hyper-V system, including Azure.
There are three versions of Hyper-V available:
- Hyper-V Server: a stand-alone product created for managing dedicated and virtual server instances
- Hyper-V for Windows 10: a product you can run on your laptop or desktop
- Hyper-V for Windows Server: an add-on for Windows Server




















0 Comments:
Post a Comment