Open Source Rats
| Tweet |
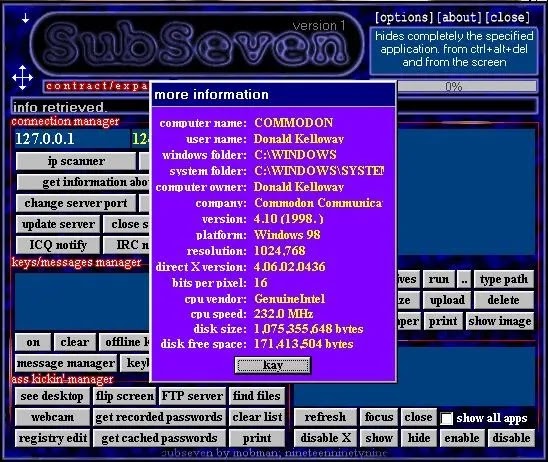
A remote access trojan (RAT, sometimes called creepware) is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, “RAT” connotes criminal or malicious activity. A RAT is typically installed without the victim’s knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software and other anti-virus software.–Wikipedia On many underground forums, there is a lot of offers for RAT’s. There are cheap ones and some really expensive. Some of them are sold as service with monthly/yearly subscription. In most cases they do the same. Here are some example features: Task Manager File Manager Startup Manager Remote Desktop Remote Shell Remote Execution System Information Registry Editor System Power Commands (Restart, Shutdown, Standby) Keylogger (Unicode Support) Reverse Proxy (SOCKS5) Password Recovery (Common Browsers and FTP Clients) Clipboard Text RATs are typically client-server programs. Server part is located on hacker computer/server and client part is installed on victim computer. On the server, we can view the list of infected clients and manage them and perform all functions offered by RAT. In server software you have option to build client with all your parameters, like server address, process name, option to detect virtual environment and sandboxes etc. Some of the RATs offer also crypters and binders. Crypters and binders can be also found as separate software. A crypter is a software that is used to hide malware so that it is not easily detected by antivirus software. To perform its function, it can use encryption techniques and sometimes obfuscation. The crypter takes the executable file and obtains a new executable file which, when run, decrypts the encrypted code it contains and obtains the old original executable file. File binders are utility software that allow a user to “bind” multiple files together resulting in a single executable. For example, you can merge your encrypted client file to a 7zip installation file, or an image, sound file etc. RATs are written in various programming languages, offer different functions and are prepared for specific platforms. |
|
A remote access trojan (RAT, sometimes called creepware) is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, “RAT” connotes criminal or malicious activity. A RAT is typically installed without the victim’s knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software and other anti-virus software.–Wikipedia
On many underground forums, there is a lot of offers for RAT’s. There are cheap ones and some really expensive. Some of them are sold as service with monthly/yearly subscription. In most cases they do the same. Here are some example features:
Task Manager
File Manager
Startup Manager
Remote Desktop
Remote Shell
Remote Execution
System Information
Registry Editor
System Power Commands (Restart, Shutdown, Standby)
Keylogger (Unicode Support)
Reverse Proxy (SOCKS5)
Password Recovery (Common Browsers and FTP Clients)
Clipboard Text
RATs are typically client-server programs. Server part is located on hacker computer/server and client part is installed on victim computer. On the server, we can view the list of infected clients and manage them and perform all functions offered by RAT.
In server software you have option to build client with all your parameters, like server address, process name, option to detect virtual environment and sandboxes etc. Some of the RATs offer also crypters and binders. Crypters and binders can be also found as separate software.
A crypter is a software that is used to hide malware so that it is not easily detected by antivirus software. To perform its function, it can use encryption techniques and sometimes obfuscation. The crypter takes the executable file and obtains a new executable file which, when run, decrypts the encrypted code it contains and obtains the old original executable file.
File binders are utility software that allow a user to “bind” multiple files together resulting in a single executable. For example, you can merge your encrypted client file to a 7zip installation file, or an image, sound file etc.
RATs are written in various programming languages, offer different functions and are prepared for specific platforms.















0 Comments:
Post a Comment